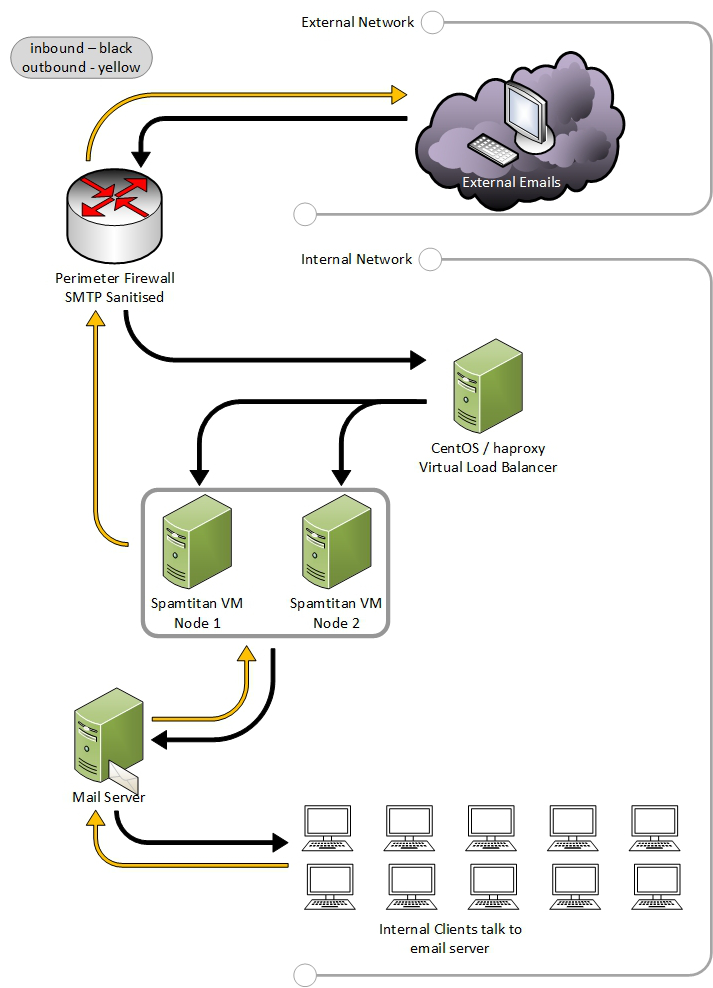
Simple method to load balance TCP traffic (SMTP in this case)
Open-source solution (CentOS VM running haproxy) – stats can easily be viewed through the load balancer web portal.
Problem
Needed a simple solution to load balance inbound SMTP across my evaluation Spam Titan nodes (looking for a more efficient and secure email filtering system than currently in use).
- Two cluster nodes running as VMs
- Outbound Port 25 load balanced by the mail servers through the cluster
- Inbound only going through one node (firewall limitation on Port 25 forwarding)
Solution
haproxy on Linux (CentOS) – some incarnations of Linux include it already.
Simplified mail flow diagram
Spam Titan on-site evaluation
Already had a host I could run it on as a VM and as all open-source, essentially completely free.
- Built new Centos 6.6 VM on Hyper-V (built a few 6.6 and 7 recently, took 15 minutes)
- Logged in as root, installed epel-release and haproxy (yum install epel-release haproxy -y)
- Modified haproxy.cfg as below, modified iptables to permit TCP ports 25 and 8080
- Pointed inbound smtp to the IP of the load balancer
Works an absolute treat..! Not going to be a permanent solution as once confirmed it performs as required we’ll be going for the private cloud solution, not on-site.
Test
Open a few Telnet sessions to the Load Balancer IP on Port 25 – each attempt should actually connect to the cluster nodes alternately
Stats
You can monitor the load balancer though its web interface as configured in haproxy.cfg
http://load_balancer_IP:port/haproxy_stats
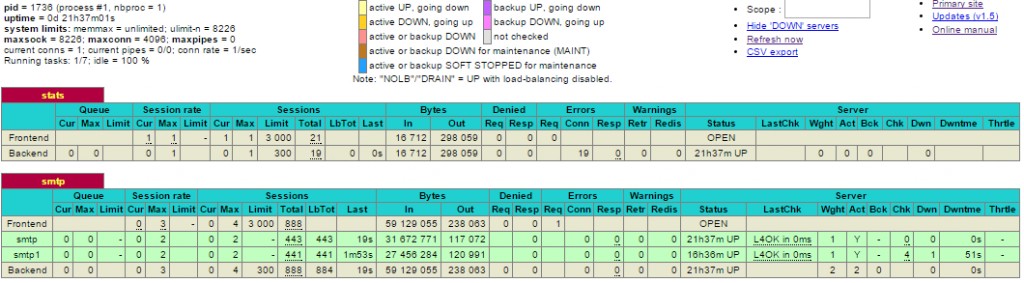
HAProxy stats screenshot – running on Centos 6.6
haproxy.cfg – /etc/haproxy/haproxy.cfg
Copy and paste the below over your haproxy.cfg – changing the IP addresses to your own.
I believe you can have up to 4 servers as back-end (only two here – my spamtitan nodes).
#———————————————————————
# Example configuration for a SMTP Load Balancing
#———————————————————————
#———————————————————————
# Global settings
#———————————————————————
global
# to have messages logged in /var/log/haproxy.log :
#
# 1) configure syslog to accept network events by adding ‘-r’ to SYSLOGD_OPTIONS:
# /etc/sysconfig/syslog
#
# 2) configure local2 events to go to the /var/log/haproxy.log:
# local2.* /var/log/haproxy.log
#
log 127.0.0.1 local0
log 127.0.0.1 local1 notice
chroot /var/lib/haproxy
maxconn 4096
user haproxy
group haproxy
daemon
# turn on stats unix socket
stats socket /var/lib/haproxy/stats
#———————————————————————
# common defaults for ‘listen’ and ‘backend’ sections if not designated in their block
#———————————————————————
defaults
mode http
log global
option httplog
option dontlognull
option redispatch
retries 3
timeout http-request 10s
timeout queue 1m
timeout connect 10s
timeout client 1m
timeout server 1m
timeout http-keep-alive 10s
timeout check 10s
maxconn 3000
# Bind to IP for stats browsing
listen stats load_balancer_IP:8080
balance
mode http
stats enable
stats realm HAProxy\ Statistics
stats auth admin:yourpasswordhere
stats uri /haproxy_stats
# Bind port to IP for listening
listen smtp load_balancer_IP:25
mode tcp
option tcplog
balance roundrobin
server smtp smtp_server_1_IP check
server smtp1 smtp_server_2_IP check
You don’t speak about see the source IPs from internet for spam filtering with DNSBL ?
Correct – it’s just a brief post about the concept of port 25 load balancing with haproxy. This was just a temporary work-around but I thought it interesting enough to comment about.